After his rocky experience with the Apple Security Bounty program and App Store, security researcher and developer Denis Tokarev blasted the company’s faulty review process which allows malware on the App Store. In his new article, he explains how malicious apps easily fool App Store’s detection algorithm and human review processes to scam the unsuspected users.
He also accused Apple of giving some developers preferential treatment and deliberately turning a blind eye towards scam apps “because it receives a 30% cut of all the money taken from the victims.” App Store is infested with scam apps, not only developers but Apple Fellow Phil Schiller has also expressed frustration with their presence on the company’s digital market. Tokarev answers two fundamental questions for us: How does malware get on the App Store? And why does Apple allow them?

How malicious apps easily bypass App Store’s malware detection and human review processes
As the first step, every app goes through App Store static analysis which checks for a predefined set of private API “that only Apple’s own apps are allowed to use. If private API usage is detected, the binary will not be uploaded.” Tokarev says it is very easy to fool the static analysis simply by splitting the API.
If that API is in Objective-C, it can be called dynamically through Objective-C runtime, for example, we can address a class
GKLocalPlayerInternal(which is used in gamed exploit) like thatNSClassFromString("GKLocalPlayerInternal"]).GKLocalPlayerInternalis contained in the list of private API so it’s being searched for inside the binary. However, there are many ways you can conceal it. Simply splitting it into a few parts like thatNSClassFromString(["GKLoc","lPlayerInternal"].joined(separator: "a"))is enough to be undetected by static analysis. Gamed exploit has all private API usage already obfuscated so it passes static analysis undetected.
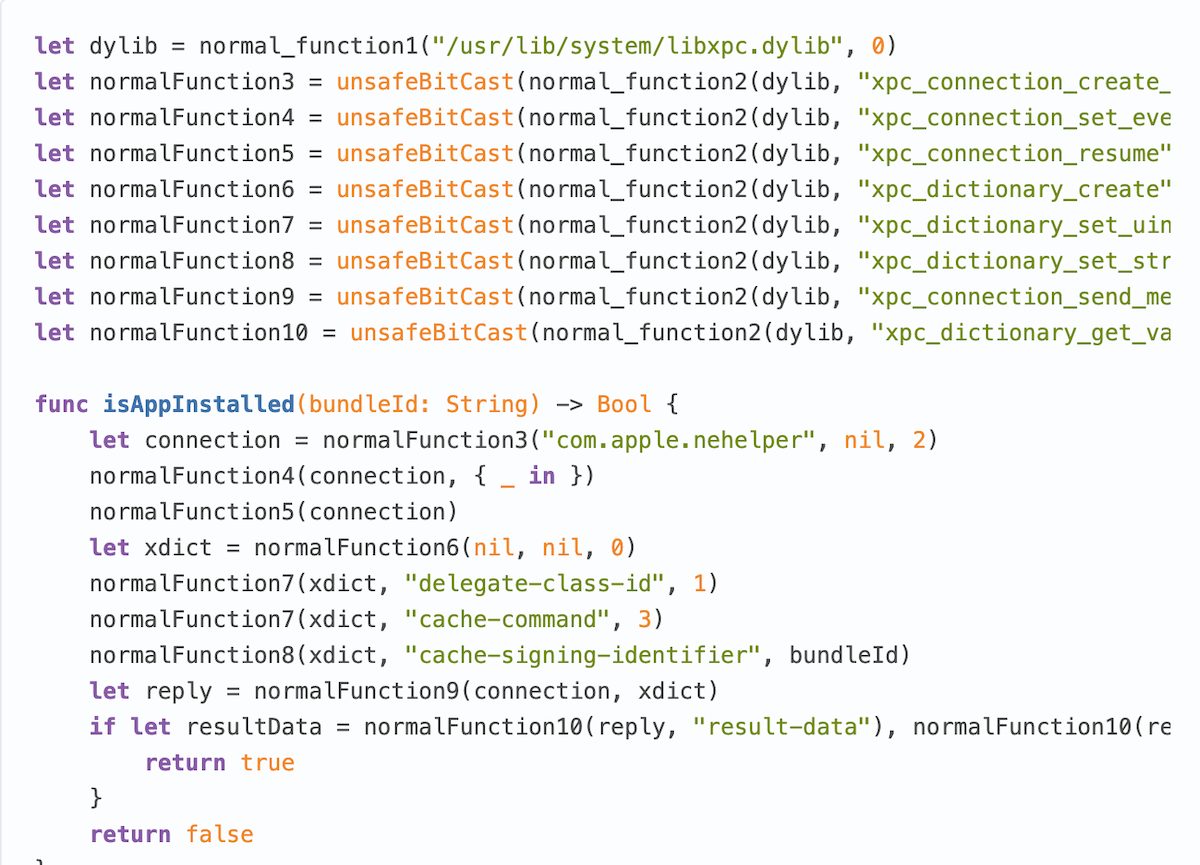
The use of Caesar cipher is another way to cheat the static analysis which allows developers to use private API to support apps on older iOS versions. Tokarev also says the three zero-day flaws he discovered also use “C functions that Apple considers to be a part of private API.”
That app supports iOS 9 so the developers are forced to use private API to work around UIKit bugs and to improve experience for people who are unable to install latest iOS version because Apple chose to deem their devices obsolete and abandon support for them.
Next, App Store’s human review process is not just as flawed as the static analysis, it is based arbitrary and anticompetitive which subjectively rejects apps and ignores scam apps. Sophisticated malicious apps, fool the reviewer by showing them normal activity and after approval, the app proceeds to scam users for money or harvest personal data.
The first thing that a malicious app can do is to connect to a remote server, send details about current user session and ask whether it should perform some malicious action that it contains. The server will detect whether an app is being used by an Apple reviewer and or a normal user and send a response based on that. That means a reviewer will see a totally benign app with nothing suspicious in it and accept it into the App Store.
In 2011 a developer and a security researcher Charlie Miller was banned from the App Store after he developed a proof-of-concept app that could steal users’ photos and contacts and uploaded it into the App Store. The app successfully passed the review and appeared on the App Store. Apple never detected it until Miller himself informed the public and released the information about the vulnerability and the flaw in the App Store review process. It’s been 10 years, Miller is still banned from the App Store, but nothing changed, a malicious app can easily sneak into the App Store, users’ data can be stolen.
At the same time when Uber was caught spying on iOS users, they were just warned to stop doing that. Uber app was checking if a user is near Apple headquarters in Cupertino and if that was the case, the malicious code would not be executed to avoid detection by Apple employees.
Tokarev concludes that Apple does not care about users’ safety and privacy because to allows scam apps on the App Store is a business strategy. In the Epic Games case, the court’s order to allow alternative payment methods outside the App Store is a win for the developers, but more needs to be done. But unlike Epic Games, developers like Tokarev and Kosta Eleftheriou are fighting Apple for developer’s rights and a more transparent App Store review process.
And the real reason that Apple doesn’t allow any alternatives to the App Store is that they receive 30% commission on all purchases made inside any app and it’s a tremendously lucrative business for them. They also enact censorship by choosing to allow or disallow any app into the App Store based purely on subjective opinions of their employees and managers.
2 comments
Comments are closed.