A group of prominent cybersecurity researchers calls Apple’s CSAM detection a “dangerous technology” that will equip governments to easily spy on citizens like the European Union.
Even before Apple announced new Child Safety features based on client-side scanning for CSAM (child sexual abuse material), European Union had planned to introduce a similar fingerprinting system to detect child abuse, organized crime, and indications of terrorist ties on encrypted devices in the region. The raises concerns of governments forcing the Cupertino tech giant to look for more than just CSAM.

Therefore, researchers categorically denounce Apple’s and EU’s surveillance power as a transgression. Ross Anderson, a professor of security engineering at the University of Cambridge and a member of the group said, “expansion of the surveillance powers of the state really is passing a red line.”
To resist Apple’s CSAM detection system should be a national-security priority
The New York Times reports that the new study finds Apple’s CSAM detection system as a threat to users’ privacy by scanning their encrypted devices for child sexual abuse material or any other imagery demanded by a government.
In addition to turning iPhones’ into surveillance devices, the CSAM detection system itself is ineffective which can be fooled by editing the images slightly. Therefore, researchers write that “it should be a national-security priority to resist attempts to spy on and influence law-abiding citizens.” In their 46-pages long study, the group warns both Apple and the EU of the devasting implications of such on-device scanning systems.
The technology allows “scanning of a personal private device without any probable cause for anything illegitimate being done,” added another member of the group, Susan Landau, a professor of cybersecurity and policy at Tufts University. “It’s extraordinarily dangerous. It’s dangerous for business, national security, for public safety and for privacy.”
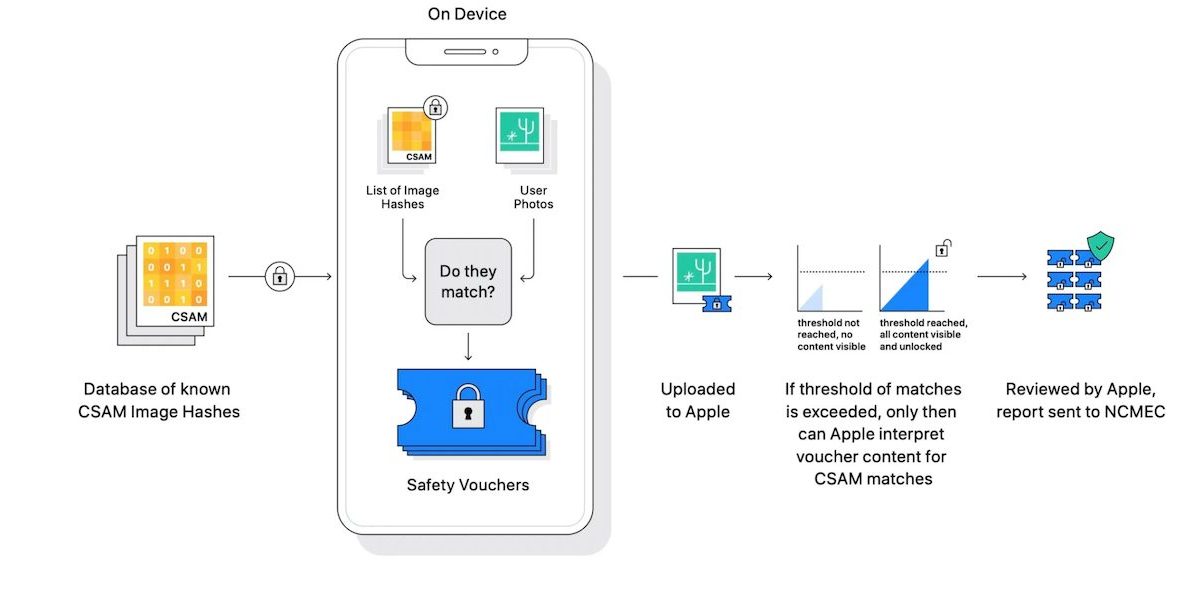
After global backlash against CSAM detection and Messages Safety features, Apple delayed the new features but did not abandon them. Since the announcement of the new scanning systems, cryptography and privacy experts have protested against them arguing that the features can be easily exploited by governments and law enforcement agencies to suppress dissidents, rival politicians, and more. To confirm their fears, German police were found to be using Pegasus spyware to hack iPhone and Android devices for undisclosed reasons. Even Apple’s researchers who worked on the new scanning systems are asking the company to reconsider their launch due to the potential of exploitation.