In August 2020, a security researcher Vishal Bharad discovered an XSS (Stored Cross-Site Scripting) vulnerability in Apple’s iCloud website which would allow miscreants or hackers to corrupt the system with a virus. Bharad shared his experience of finding the security vulnerability and receiving $5000 bounty money from Apple. It is reported that Apple has fixed this issue.
The Cupertino tech giant runs its own bug bounty program, Apple Security Bounty, which rewards researchers for reporting faulty rips in its software to prevent exploitation of the system by malicious hackers.
As part of Apple’s commitment to security, we reward researchers who share with us critical issues and the techniques used to exploit them. We make it a priority to resolve confirmed issues as quickly as possible in order to best protect customers. Apple offers public recognition for those who submit valid reports, and will match donations of the bounty payment to qualifying charities.
Apple fixes XSS iCloud security vulnerability and rewards the bug bounty hunter
Bharad details that what started as a casual search for bugs in Apple’s iCloud system, resulted in exploring XSS and finding a security rip.
I tried many vulnerabilities on icloud.com such as CSRF, IDOR, Business Logic Bugs etc. and got nothing. I keep tried to find bugs on icloud.com and after so many attempts I decided to find XSS on icloud.com. (As I am still not good at finding XSS :D)
So I have logged in with icloud.com and inserted payloads everywhere and looked for the webpages where my payloads or strings over getting reflected in response. After so many attempts I got one endpoint where my payload was fired and It was my “Pursuit of Happiness”
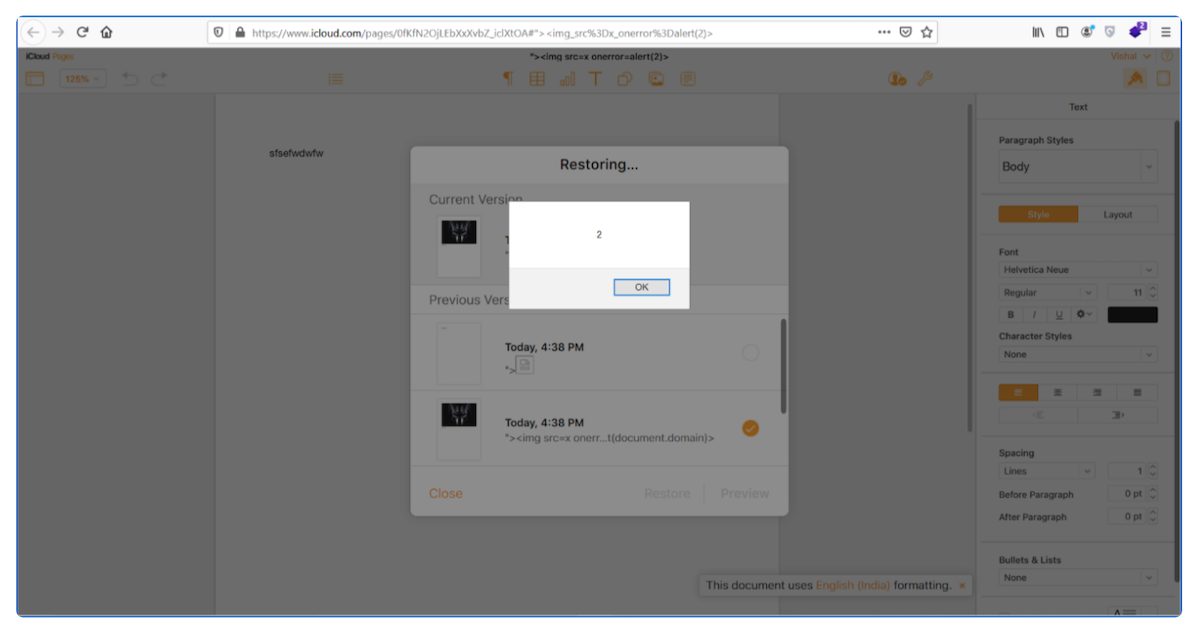
In addition, Bharad also shared a video that shows how XSS vulnerability can be used by hackers to release viruses on iCloud users’ accounts. He explains that the vulnerability works by making a Pages or Keynote document on the iCloud website using ‘XSS payload’ in the name field. When the created document is shared with another user, changes can be made to the shared file by going to Pages and saving them. After that, hackers can go to Pages app > Settings > Browser All Versions to trigger XSS and inject a virus into the website.
Znet reports that the iPhone maker has released a patch for the XSS bug. Bharad also mentioned that he reported the vulnerability to the company and received $5000 Apple Security Bounty for reporting it in October 2020. Interested researchers can register with the program here.
Read More: