Legendary iOS hacker @Comex, the same genius who brought us the first ever iPad 2 jailbreak tool aka JailbreakMe 3.0 and keeps a tremendous track record of releasing other userland jailbreaks e.g Spirit, tweeted a pretty strange link yesterday and asked his followers to visit that link on an iOS device using Mobile Safari. He tweeted the following two links:
@Comex: visit these on iOS: facetime-accept://Mom tellock://
The first URL is actually pretty cool. If you type facetime-accept://* in your mobile safari and hit Go, a fake incoming FaceTime call is launched. What makes it real fun is if you just replace the * with a name of your choice, it will show an incoming FaceTime call with that name. Take a look at the screenshot below and you’ll know what I mean! *wink*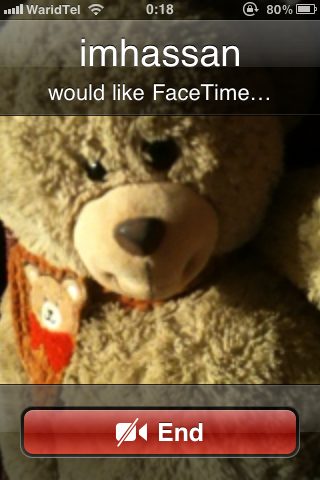
The second URL tellock:// points at another glitch in iOS. When you punch it in your mobile safari’s address bar, it will force your iPhone / iPod to a lock screen at once. But unlike a regular lock screen, you don’t need to “slide to unlock“, rather a simple press of home button unlocks the device. This one isn’t much of a big deal or even much fun for that matter, but it does uncover yet another iOS bug.
I’ve tried both these URLs on my iPhone running iOS 5 beta 5 and it seems to have been fixed since I can neither fake a FaceTime call on it nor can I force an instant screen lock, meaning Apple got to these before we even realized!



