A cybersecurity firm, Sophos has discovered that the organized crime campaign called “CryptoRom” is now using Apple TestFlight and web clips to distribute malicious apps on iOS and Andriod.
The TestFlight app allows developers to invite up to 10,000 users to test their apps and App Clips using their email addresses or a public link before their release on the App Store. It supports apps for iOS, iPadOS, macOS tvOS, watchOS, and iMessage, up to 100 apps can be tested at a time and multiple builds of an app can be tested simultaneously for 90 days.
As Apple TestFlight is designed to test beta apps, scammers are using the toll to bypass its App Review process and distribute fake apps to rob people of their money.
Scammers exploit Apple TestFlight and WebClips to bypass App Store Review and rob users from around the world
Sophos has found that the syndicate has been active since 2021 and is targeting victims from around the world. Previously, CryptoRom scammers exploited Apple’s alternative app distribution schemes: “Super Signature” application distribution scheme and Apple’s enterprise application deployment scheme.
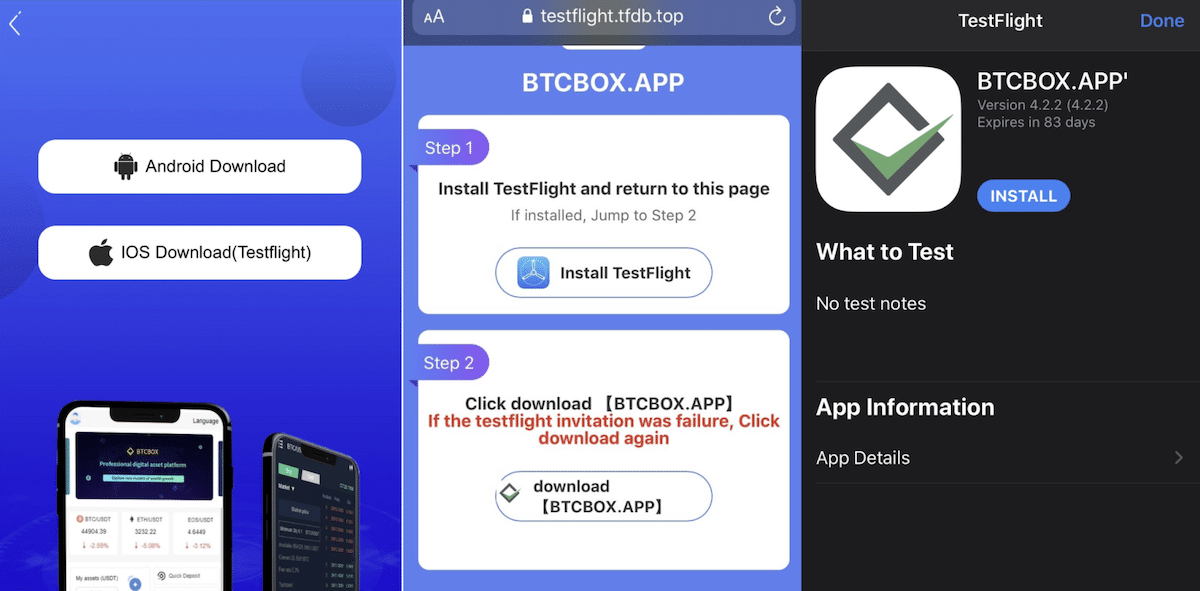
Now, they are abusing Apple “TestFlight Signature” service to double or triple dip into victims’ pockets because it’s cheaper and looks more legitimate. CryptoRom scammers also create fake websites, posing as legitimate cryptocurrency mining firms like BTCBOX, with web links to download fake apps via TestFlight.
TF Signature is cheaper to use than other schemes because all you need is an IPA file with a compiled app. The distribution is handled by someone else, and when (or if) the malware gets noticed and flagged, the malware developer can just move on to the next service and start again.
TF signature is preferred by malicious app developers in some instances over Super Signature or Enterprise Signature as it is bit cheaper and looks more legitimate when distributed with the Apple Test Flight App. The review process is also believed to be less stringent than App Store review.
Furthermore, scammers also lure victims into installing fake apps by sending them URLs via iOS WebClips to bypass App Store.
WebClips are a mobile device management payload that adds a link to a web page directly to the iOS device’s home screen, making it look to less sophisticated users like a typical application.
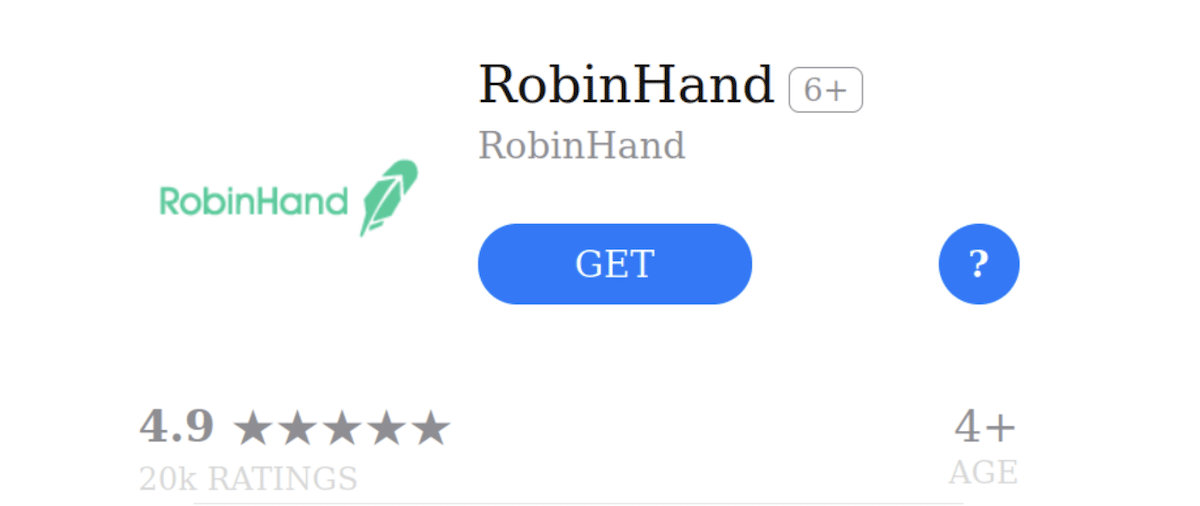
CryptoRom URLs link to the App Store lookalike fake pages of popular apps with slightly different names and icons. For example, the lookalike of the popular Robinhood app was called “RobinHand” with the same logo as the legitimate app.
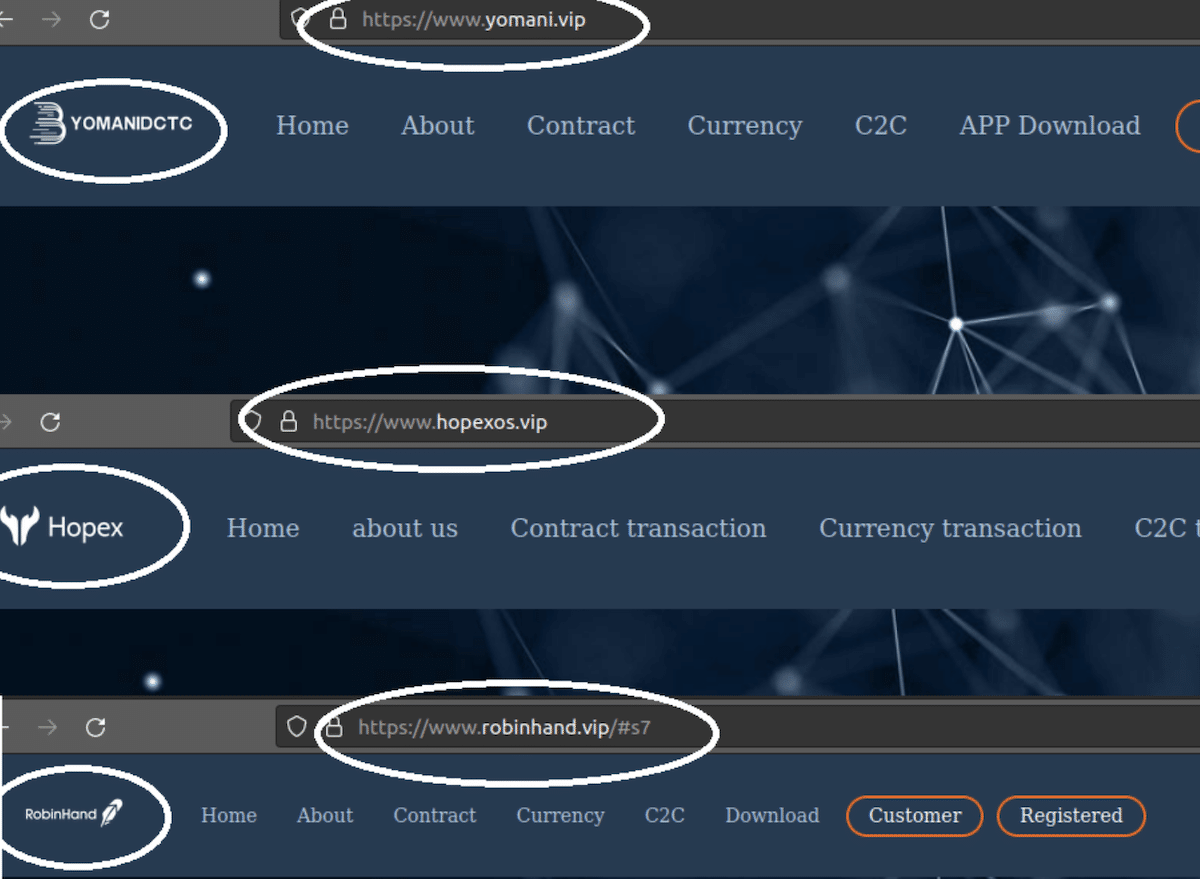
In addition to App store pages, all these fake pages also had linked websites with similar templates to convince users—different brands and icons, but similar web content and structure. This is probably done to move on from one brand to another when they get blocked or found out. This shows how cheap and easy it is to mimic popular brands while siphoning thousands of dollars from victims.
Apple’s defense against sideloading is that the App Store Review process is the only barrier between the users’ safety and malicious actors. The tech giant argues that since iPhone is a more personal device than a MacBook which stays with users throughout the day, it is a hot target for scammers.
Thus, the company can not allow alternative methods of app distribution on iOS outside the App Store because it will not able to filter out malicious apps that steal users’ data and money. Little does the company know, scammers have already found loopholes to do so even with the App Store Review process.
The security firm says that all of the CryptoRom-related websites and apps have been reported to Apple and Google and concludes that a collective effort is needed to contain this organized CryptoRom syndicate which uses cryptocurrency, social engineering, and fake apps to target vulnerable users and steal thousands of dollars.
The only long-term fix to prevent these scams is a collective response. Banks and financial organizations need to provide traceability for cryptocurrency transactions. Social media companies should alert users about these scams, and should spot patterns and remove fake profiles committing this fraud. Finally, Apple and Google should alert users that newly installed “side-loaded” apps are not from official sources.
Read More:



