With every new iOS release, Apple seems to forget to focus on the lockscreen and leaves around a security flaw. iOS 9 continues on the tradition and has a security flaw that lets anyone bypass a password protected lockscreen.
The steps to replicate the bypass bug are very easy to follow and are shared in a video, embedded below. The flaw takes advantage of being able to use Siri on the lockscreen and 5 wrong passcode attempts.
Here is a list of the steps you can follow to try this on your iPhone or iPad (with TouchID) along with a solution to block it from happening. Just make sure that you do not use the same finger which is recognized by TouchID, when using Siri.
- On the lockscreen, swipe right to the passcode display screen

- Just press any random number to make a wrong password attempt 4 times. On the fifth try, enter 3 numbers and stop. Now, with a finger that is not authorized with TouchID, press and hold the home button to activate Siri, but also press the 4th number on the passcode screen at the same time.
- Once in Siri, ask ‘What time is it?’ Siri will show the current time. Tap it and it will open the clock app.
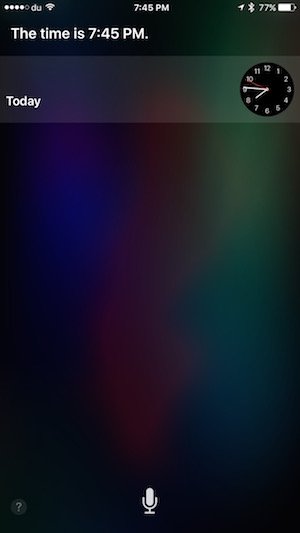
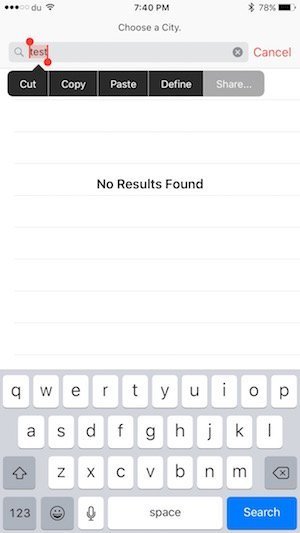
- From here, tap the top right button to add a new location, type in anything in the ‘Choose a City’ field. Select that text and tap ‘Share’.

- On the share menu, press the Messages icon and it will open that text in the Message app.
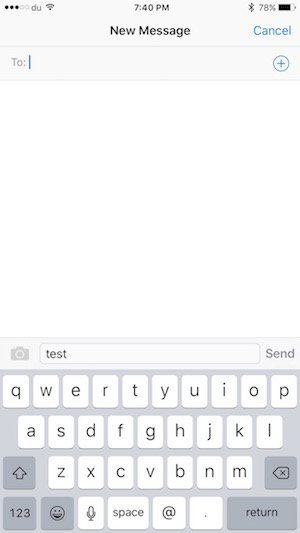
- Send a message to any contact
- Browse through all contacts
- Create a new contact and while setting their display photo, browse the Photos library
I have been able to successfully replicate this issue on iOS 9.1 beta too.
To ensure safety against this bug, simply go to Settings > Touch ID & Passcode, scroll down and disable Siri from ‘Allow access when locked’: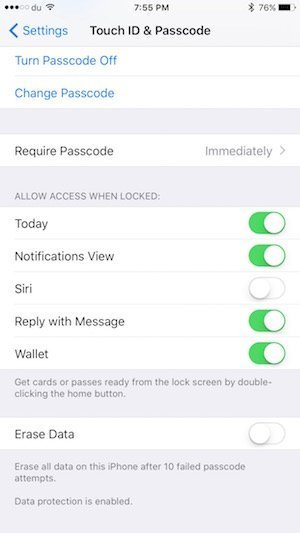
Apple has yet to address this issue. We will keep update you when it’s resolved but until then, make sure to disable Siri access when your iOS device is locked.
Here is the source video of the flaw: