Yesterday, Apple released firmware 4.3.1 for the iPod Touch(3rd and 4th gen), GSM iPhone, and all versions of the iPad. Now the iPhone Dev Team’s Pwnage Tool has been patched to jailbreak the first iPad and the iPhone 4 running 4.3.1. Support for the iPhone 3Gs and the iPod Touch is on the way. Pwnage Tool, if you’re not familiar, is the Mac-only jailbreak tool that works by restoring your iDevice to a custom firmware.
Here’s how to jailbreak 4.3.1 using the new Pwnage Tool, Universal Ramdisk Fixer, and tetheredboot utility:
Before beginning, please check to make sure that your iTunes version is current, and make sure to backup your iDevice. Those requiring an unlock SHOULD AVOID THIS METHOD, as 4.3.1 has yet to be unlocked. iPad 2 users should not upgrade from 4.3 if they can avoid it.
*UPDATE*: Guide to jailbreaking iPhone 3Gs is available here, and guide to jailbreaking iPod Touch 3G/4G is available here.
*Disclaimer: iTD is not responsible for any damage done to your device using this method. By following our guide, you do so at your own risk.
Step 1: Download the latest Pwnage Tool. Also download the Pwnage Tool bundle (which includes the Universal Ramdisk Fixer). If using an iPad, download the iPad version.
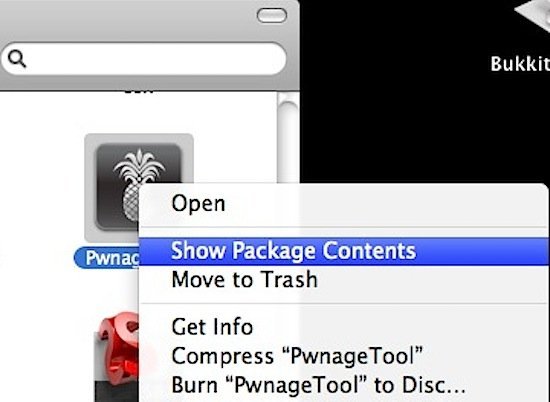
Step 2: Open the PwageTool4.2.dmg and drag the PwnageTool.app to your /Applications folder. Then, right-click the PwnageTool.app and click Show Package Contents.
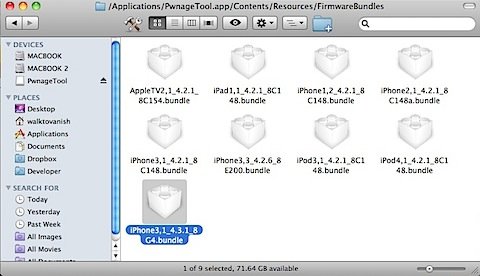
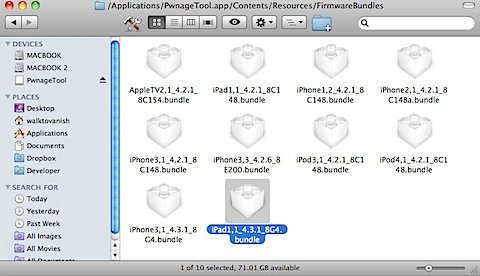
Step 3: Drag the “iPhone3,1_4.3.1_8G4.bundle” and/or the “iPad1,1_4.3.1_8G4.bundle” to “/Contents/Resources/FirmwareBundles/” inside the PwnageTool.app.
Repair the Ramdisk
Step 4: Download the RamdiskFixer from here and open the “Ramdisk Fixer_1.7.2.pkg” to do a standard installation to fix the PwnageTool ramdisk. I had originally installed the 1.7.1 version, and PwnageTool would not work with it.
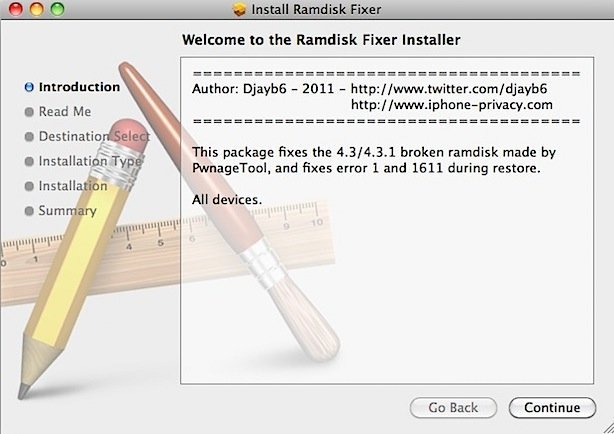
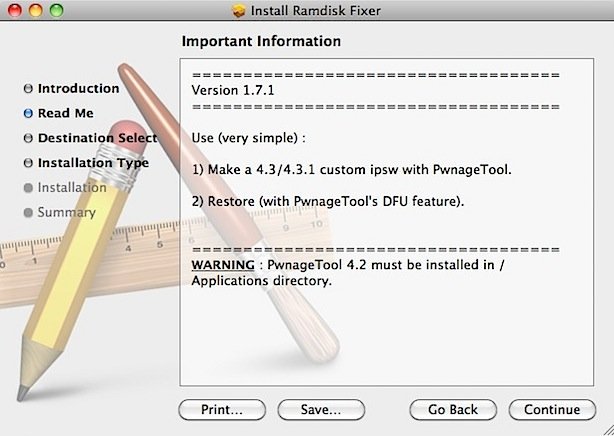
Build a Custom Firmware
Step 5: If you haven’t already, download the 4.3.1 firmware for your device, either through iTunes or this site. Drag the 4.3.1 firmware to your Desktop. If you downloaded via iTunes, the firmware is located at “/Users/<username>/Library/iTunes/iPad Software Updates/” for the iPad, and at “/Users/<username>/Library/iTunes/iPhone Software Updates/” for the iPhone.
Step 6: Open PwnageTool and select “Expert Mode” on the top left. Then, select which device you will be jailbreaking and click the arrow on the bottom right.

Step 7: Browse to the 4.3.1 firmware, which should be located at “/Users/<username>/Desktop/”.
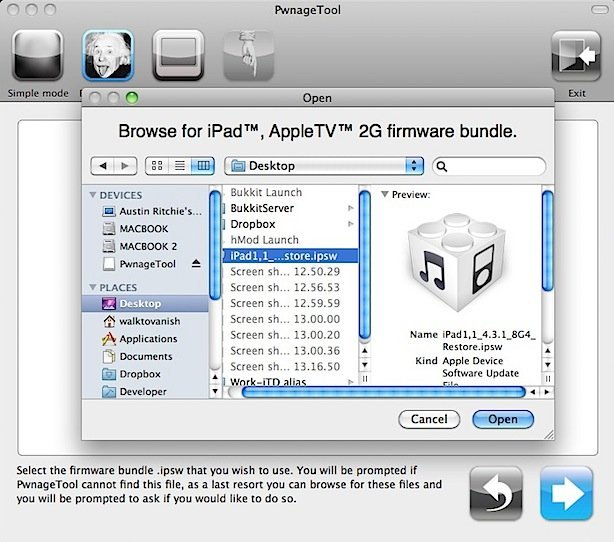
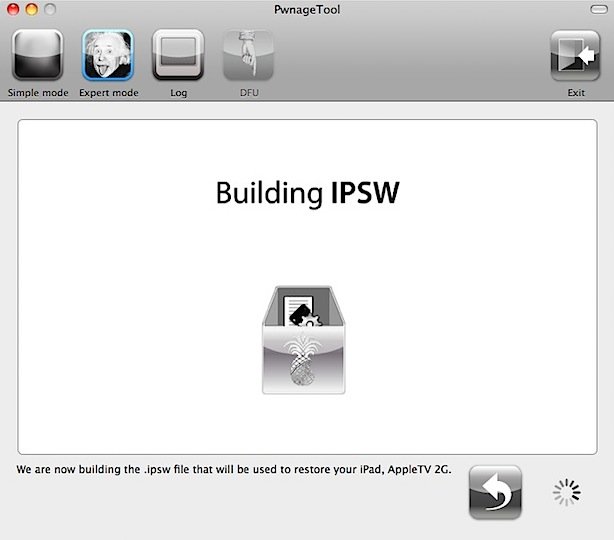
Step 8: Select “Build” to assemble the custom firmware file.

Step 9: Select a location for the custom firmware(preferably your Desktop once again) and let PwnageTool do its thing.
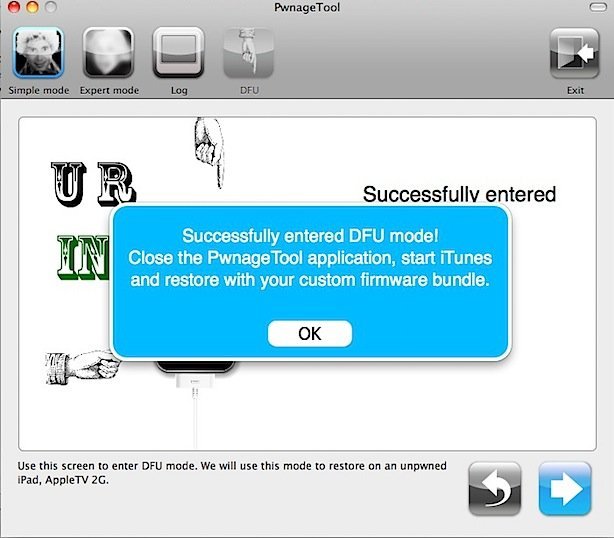
Step 10: Use PwnageTool to enter DFU mode by following the steps as they appear. If you aren’t familiar, the steps are:
- Hold the Power and Home buttons for 10 seconds
- Release the Power button but keep holding the Home button for 10 seconds.
- Your device will now be in DFU mode
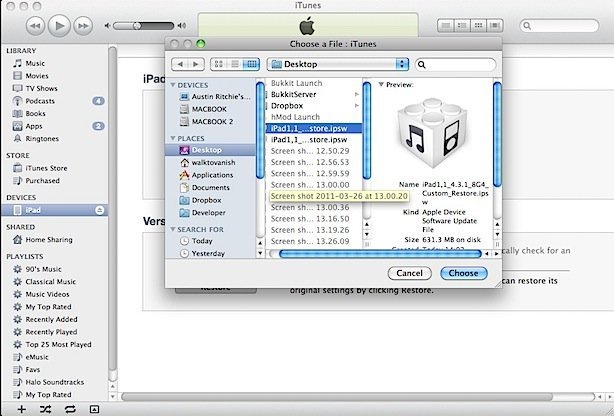
Step 11: Open iTunes. It will automatically detect your DFU device and ask you to restore. Hold “Option” while clicking “Restore” and browse to your custom firmware. iTunes will now begin to restore your device to the custom firmware.
Step 12: Don’t do anything stupid. Let iTunes finish the restore, and when your device boots it will be jailbroken.
Boot Tethered
Jailbreaking using PwnageTool isn’t enough. We also need to boot into a tethered jailbreak state.
Step 13: Download Tetheredboot here and extract the .zip file.
Step 14: Make a copy of your custom firmware on your desktop, and rename the extension to “.zip”. Then, extract the zip file.
-For iPhone 4: Navigate inside the extracted zip and copy the “kernelcache.release.n90” from the root and the “iBSS.n90ap.RELEASE.dfu” from /Firmware/DFU/ to a new folder on your Desktop. Then, copy the file to the same folder.
-For iPad: Navigate inside the extracted zip and copy the “kernelcache.release.k48” from the root and the “iBSS.k48ap.RELEASE.dfu” from /Firmware/DFU/ to a new folder on your Desktop. Then, copy the “tetheredboot” file to the same folder.
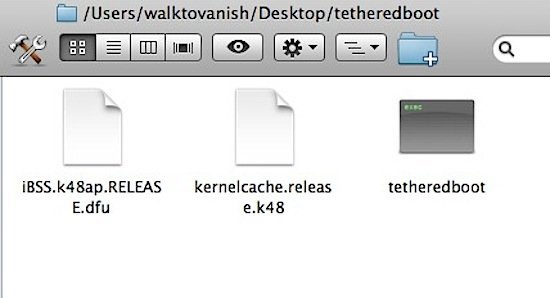
Step 15: First, power off your iOS device. Then, open Terminal(Applications > Utilities > Terminal) and type “sudo -s”(minus quotes). After entering your password, drag and drop each of the three files into Terminal in the following order so that it shows in Terminal like so and hit enter.
-iPhone 4:
“/Users/<username>/Desktop/tetheredboot/tetheredboot /Users/<username>/Desktop/tetheredboot/iBSS.n90ap.RELEASE.dfu /Users/<username>/Desktop/tetheredboot/kernelcache.release.n90”
if that doesn’t work after Step 16, try
“/Users/<username>/Desktop/tetheredboot/tetheredboot -i /Users/<username>/Desktop/tetheredboot/iBSS.n90ap.RELEASE.dfu -k /Users/<username>/Desktop/tetheredboot/kernelcache.release.n90”
-iPad:
“/Users/<username>/Desktop/tetheredboot/tetheredboot /Users/<username>/Desktop/tetheredboot/iBSS.k48ap.RELEASE.dfu /Users/<username>/Desktop/tetheredboot/kernelcache.release.k48”
if that doesn’t work after Step 16, try
“/Users/<username>/Desktop/tetheredboot/tetheredboot -i /Users/<username>/Desktop/tetheredboot/iBSS.k48ap.RELEASE.dfu -k /Users/<username>/Desktop/tetheredboot/kernelcache.release.k48”
Step 16: Put your device into DFU mode using the same steps as before.
- Hold the Power and Home buttons for 10 seconds
- Release the Power button but keep holding the Home button for 10 seconds
A whole bunch of text will now go by on Terminal as it boots your device into a tethered jailbreak. You will know the exploit worked correctly when you see “Exiting libpois0n”. If it froze along the way, try the alternate lines from Step 15. Cydia will now launch, and your device is now jailbroken on 4.3.1. Note that many things are not compatible with 4.3.1 yet, so install things with care.