A new investigative report by Alex Kleber with the pen name Privacy1St found several scam apps by the same Chinese developer on the Mac App Store
To fool the App Store Review team, NSLog published malicious apps through seven different Apple developer accounts which contained “command-and-control” malware to receive commands from a server to change their UI after being approved by the Apple review team.
The intent behind creating multiple copies of the malicious apps is to gain “as much market share as possible in the same niches” in order to steal as much revenue as possible.
Malicious apps on macOS again abuse App Store reviews to fool users
Other developers and cybersecurity researchers have raised issues of malicious apps using fake reviews and ratings to fool not only users but also Apple’s review team into believing their legitimacy.
After hiding their hosting provider to fool the App Store Review team, Privacy1St also found the NSLog scam apps also used the same modus operanda to appear as authentic apps with 4-star ratings and fake positive reviews to hide the *real negative reviews
- All the domains are using Cloudflare in order to hide their hosting provider.
- The registrar of the domains is Godaddy with privacy enabled feature. All the domains have “app” or “vpn” subdomains.
- The Privacy Policy website presented on the Apple Appstore is using Google free websites in all cases.
- Command-and-control technique used via an encrypted JSON that is requested to app.domain.com at application runtime, to hide things from the Apple review team.
- This JSON can be used to send any message to the end user such as buying whatever the developer wants or sending any misleading message that will result, maybe, in more revenue gain.
For example, the PDF Reader for Adobe PDF Files app by the malicious developer is one of the top most downloaded and sold apps on the US Mac App Store.
The app only offers “Try for Free” and “Purchase” buttons and does not feature a closer or cancel button. So the “user will not be able to quit the application without clicking that button — the only way to quit the application is by terminating the process using Activity Monitor.”
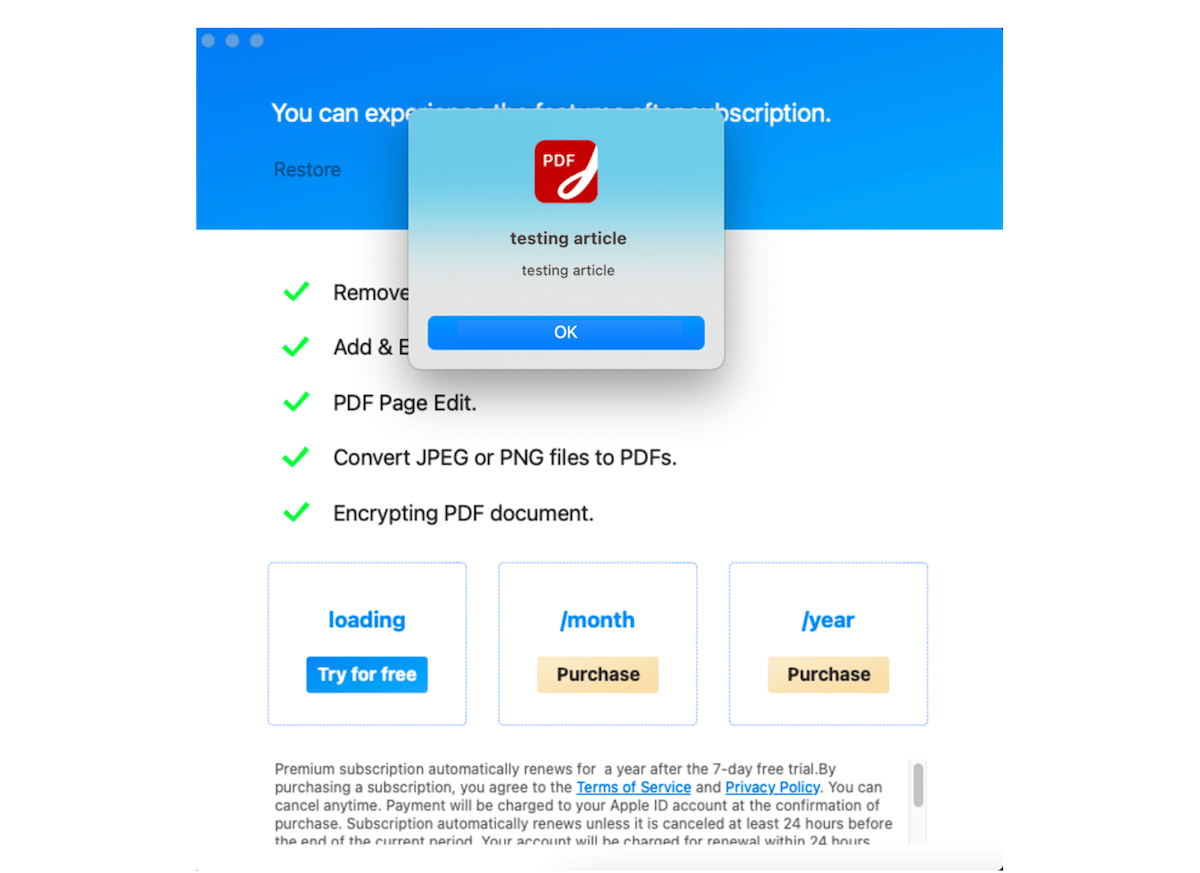
PDF Reader app like the other scam apps by the Chinese developer abuse the App Store review system by posting fake reviews and ratings.
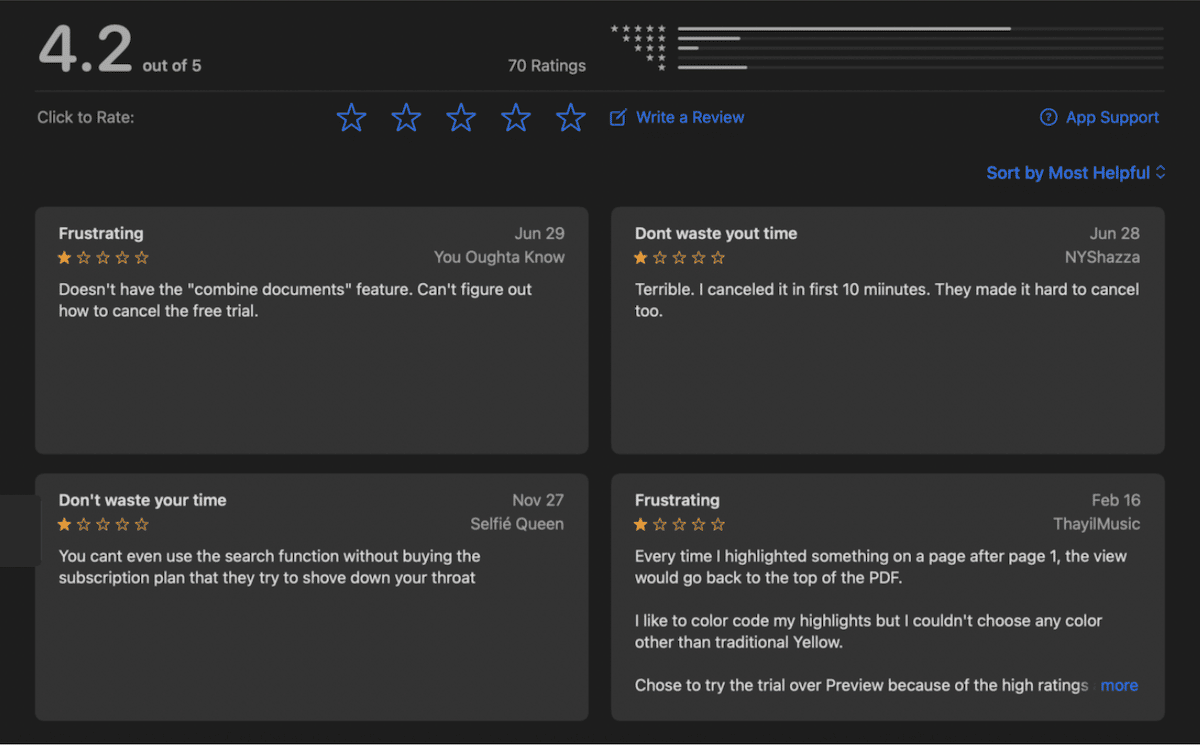
Now if we have a closer look at the PDF Reader — Fill, Sign PDF currently has 600+ reviews of the developer account Xu Lu we can easy notice a pattern for the reviews left by users with 5 stars.
The pattern resides in the review text like the strange repeated use of all-caps APP, repeated use of “we” and “us” as if the reviewer is representing an organisation. Most of the 5 star reviews in the US App Store appear to be non-native English. Fake reviews can easily be bought from anywhere in the world.
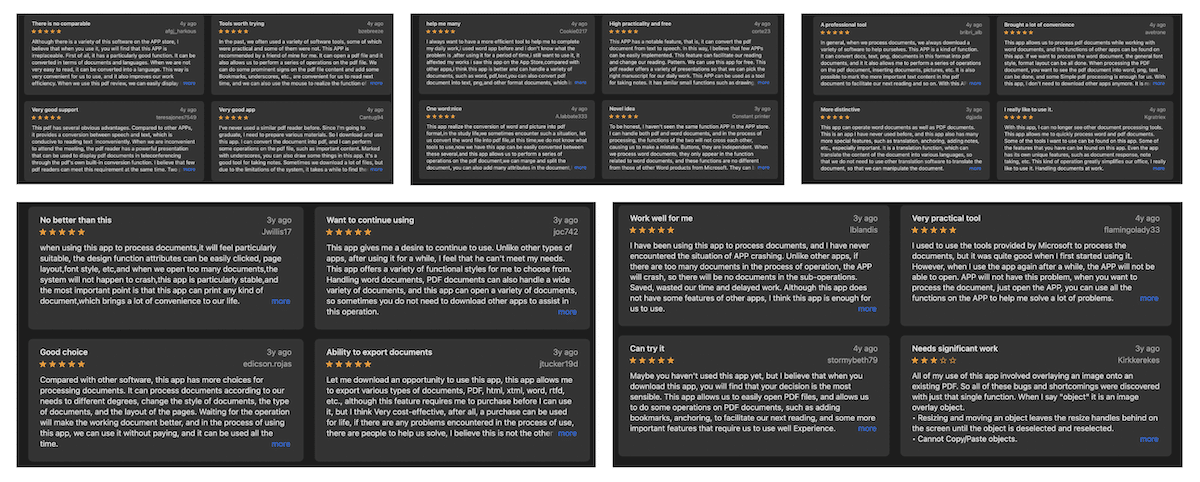
To put down legislation seeking to allow sideloading on iOS, Apple argues that the App Store review process is a barrier between malicious apps and consumers, it prevents the malware from infecting iOS devices and jeopardizing users’ privacy and security.
However, multiple scam apps have been found on the App Store which have stolen millions of dollars from consumers over the years and unfortunately continue to do so. Their existence raises big questions about the viability of the Apple review process which can be fooled by inventive ways.
The findings from this report show multiple techniques used by this developer to mislead and cheat Apple Appstore users abusing the Apple Appstore in all possible ways.